Threat Watch
Threat Watch instantly evaluates your cybersecurity posture across critical categories like credentials and dark web ...
Visit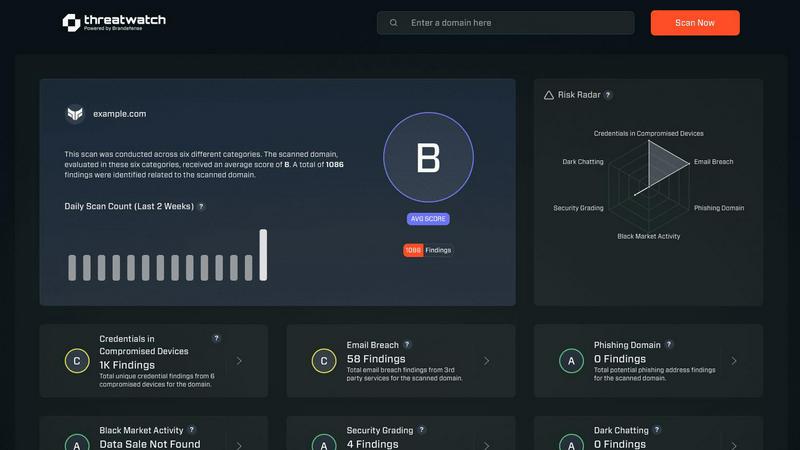
About Threat Watch
Threat Watch is a comprehensive, unified cybersecurity intelligence and exposure management platform designed for IT security teams, CISOs, and risk management professionals. It functions as a centralized diagnostic tool for an organization's external cyber health, providing continuous, automated analysis of digital assets and their associated risks. The platform's core value proposition lies in its ability to aggregate, correlate, and prioritize disparate security signals into a single, actionable overview. By continuously scanning an organization's external attack surface, Threat Watch identifies critical security issues across multiple categories, including compromised credentials, vulnerable devices, breached accounts, phishing infrastructure, and dark web exposures. This enables organizations to move from a reactive security posture to a proactive, intelligence-driven model. The solution delivers real-time insights and automated assessments, significantly reducing the mean time to identify (MTTI) and remediate (MTTR) critical vulnerabilities, thereby hardening the organization's external defenses against modern cyber threats.
Features of Threat Watch
Comprehensive Attack Surface Analysis
Threat Watch performs continuous, non-intrusive reconnaissance on an organization's publicly accessible digital footprint. This includes scanning IP ranges, domains, and subdomains to catalog all internet-facing assets. The system identifies misconfigurations, open ports, unpatched services, and shadow IT resources that could serve as entry points for attackers. This automated asset discovery and classification provide a foundational inventory that is critical for effective security posture management and risk calculation.
Credential and Data Breach Monitoring
The platform actively monitors a vast array of data sources, including underground forums, paste sites, and dark web marketplaces, for compromised employee credentials and corporate data. It correlates found email addresses, usernames, and password hashes with your organization's domains. When a match is detected, it generates an immediate alert with details of the breach source and the exposed data, allowing for swift credential rotation and account lockdown to prevent account takeover attacks and lateral movement.
Phishing & Impersonation Detection
Threat Watch employs advanced algorithms to detect phishing campaigns and fraudulent sites targeting your organization. It scans for domain names that are typo-squatting variants of your legitimate domains, counterfeit mobile applications, and fraudulent social media profiles. This feature provides early warning of active impersonation attacks, enabling security teams to initiate takedown procedures before significant brand damage or data loss occurs.
Real-Time Cyber Health Scoring & Reporting
The platform synthesizes all discovered vulnerabilities, exposures, and threats into a dynamic, quantifiable Cyber Health Score. This score provides an at-a-glance understanding of overall security posture and trends over time. Detailed, executive-ready reports break down risks by category (credentials, devices, phishing, dark web) and severity, complete with evidence and contextual intelligence to guide remediation efforts and justify security investments to stakeholders.
Use Cases of Threat Watch
Proactive External Risk Management
Security teams utilize Threat Watch to shift from a reactive, alert-driven model to a proactive risk management strategy. By continuously mapping the external attack surface and identifying exposures before they are exploited, organizations can systematically eliminate low-hanging fruit for attackers. This use case involves scheduled scanning, prioritization of vulnerabilities based on exploitability and asset criticality, and workflow integration to assign and track remediation tasks, thereby reducing the overall risk profile.
Incident Response and Breach Investigation
During a suspected or confirmed security incident, Threat Watch serves as a critical investigative tool. Teams can rapidly query the platform to determine if compromised credentials found in an incident are present in external breach databases, or if company assets were communicating with known malicious infrastructure. This provides crucial context for the scope, root cause, and attribution of an attack, accelerating containment and forensic analysis.
Third-Party and Supply Chain Risk Assessment
Organizations extend the use of Threat Watch to monitor the external security posture of key vendors and partners. By assessing the public-facing cyber health of third parties, they can identify potential weak links in their supply chain. This enables more informed vendor risk assessments and allows for constructive security conversations with partners, mitigating the risk of a supply chain attack originating from a less-secure external entity.
Compliance and Audit Readiness
For organizations bound by regulatory frameworks like GDPR, HIPAA, or PCI-DSS, Threat Watch provides continuous evidence of due diligence in monitoring for data breaches and securing external perimeters. The automated reporting and audit trails demonstrate ongoing efforts to identify and address security exposures, supporting compliance reports and simplifying the audit process by providing documented proof of security controls.
Frequently Asked Questions
How does Threat Watch discover my organization's assets without internal access?
Threat Watch operates as an external, attacker-style reconnaissance platform. It uses passive data collection from public sources (DNS records, SSL certificates, search engines) and active, non-intrusive scanning techniques against your publicly declared IP ranges and domains. No agents are installed internally, and the scans are designed to be safe and respectful of network boundaries, mimicking the perspective of an external threat actor to accurately assess what is visible and exploitable from the internet.
What is the frequency of scans and data source updates?
The platform performs continuous monitoring. Asset discovery and vulnerability scans are conducted on a configurable schedule, typically ranging from daily to weekly, ensuring new assets and changes are promptly identified. The breach and dark web data feeds are updated in real-time, with new data ingested and correlated against your monitored domains as soon as it is discovered by Threat Watch's intelligence collectors, providing near-instantaneous alerts for credential exposures.
Can Threat Watch integrate with our existing security tools?
Yes, Threat Watch is built with integration in mind. It offers API access for bidirectional data exchange, allowing it to ingest asset lists from CMDBs and export findings, alerts, and risk scores to SIEM systems, SOAR platforms, ticketing systems like Jira or ServiceNow, and other security orchestration tools. This enables automated workflow creation, such as generating a high-priority ticket when a critical vulnerability is detected on a key server.
What kind of support and expertise is required to operate Threat Watch?
Threat Watch is designed for usability by security analysts of varying skill levels. The interface presents findings in a prioritized, actionable manner with clear guidance. However, to maximize value, operational responsibility typically lies with dedicated security personnel such as a SOC analyst, vulnerability management specialist, or threat intelligence analyst. Vendor support includes onboarding, documentation, and access to technical support to assist with configuration, interpretation of results, and best practice guidance.
You may also like:
finban
Plan your liquidity so you can make decisions with confidence: hiring, taxes, projects, investments. Get started quickly, without Excel chaos.
Zignt
Zignt simplifies contract management with secure templates, seamless sharing, and automated signing for faster workfl...
AILeadz
AILeadz automates lead generation by finding, verifying, and contacting prospects using AI and a database of 450M+ em...